Updated: June 2025
Overview
This post is the second part of a 6-post series with step-by-step procedures that I use to setup a simple WordPress website on AWS. In this post, some basic security improvements are made to the AWS instance.
Note: The original version for this series was written in 2016 with EC2 servers running Ubuntu 16.04. This series has been completely updated in mid 2025. An example website, Seattle Hobbies, will be used throughout this series. The development of the Seattle Hobbies website assumes a simple low-maintenance website with low visitor count with no auto-scaling or redundancy. As such, implementation and configuration are easy. I will most likely seek the support of professional web-dev experts if I want to establish a sophisticated website that handles commerce or significant traffic with lots of site visitors.
Adding an Alternate User for SSH:
Note: Logged into AWS
If not logged in, then log into AWS SSH as ubuntu (default user) via a command line interface (e.g., terminal on the Mac or PuTTY on Windows) as described in Part 1.
Create a second user (replace user2 with your username of choice) and create the account password for user2 that will be used with sudo commands. Just hit return on all the info requests (i.e., full name, room number, work phone, home phone, other).
sudo adduser user2
Add the new user to the admin group:
sudo adduser user2 admin
Add the new users to the sudo group by editing the ‘sudoers’ file:
sudo nano /etc/sudoers
Use the arrow keys to locate the right place in the file and add the following line in the ‘User privilege specification’ section. Then, ctrl-x, y to save, and return to save.
user2 ALL=(ALL) NOPASSWD:ALL
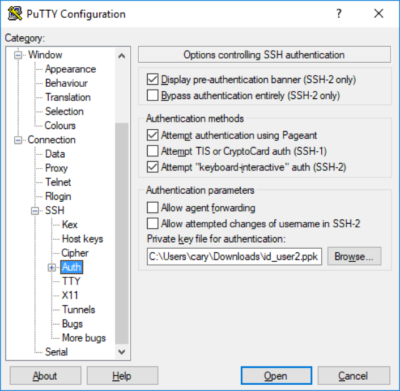
Since SSH access to an EC2 instance uses keys, keys need to be created for user2. Both the public and private keys will be created on EC2 and securely copied to the local computer that is being used to access this AWS instance via SSH. Switch to the new user2 account from the Ubuntu account and change to the user2 home directory:
su user2 cd ~
Create a .ssh directory and modify its permissions:
mkdir .ssh chmod 700 .ssh
Change to the .ssh directory and create a default (RSA 2048) key pair:
cd .ssh ssh-keygen
A filename will be requested for the key file. It should be something like: ‘id_user2’. Press the return key when prompted about the passphrase. Enter the following command to list these two files and their file properties:
ll
Two files were created id_user2 (private key) and id_user2.pub (public key). Copy the public key to an ‘authorized_keys’ file since this is a new user and ‘authorized_keys’ shouldn’t exist yet:
cp id_user2.pub authorized_keys
Clean up the permissions on these files:
chmod 600 ~/.ssh/*
Before the files can be copied to the local computer that is being used to access the AWS instance via SSH, we need to do some prep work on the AWS instance to allow access to these files from our local computer. Create a temporary directory, copy the key files (for downloading), and modify permissions:
sudo mkdir /tmp2 sudo cp ~/.ssh/* /tmp2 sudo chmod 644 /tmp2/*
Setup user2 in the ssh config file:
sudo nano /etc/ssh/sshd_config
Either change the AllowUsers line or add it:
AllowUsers ubuntu user2
Then, ctrl-x, y to save, and return to save.
Restart the ssh service:
sudo systemctl restart ssh.service
Exit out of AWS remote terminal using ‘exit’ commands (once to exit from user2, second time to exit from Ubuntu and close the AWS SSH connection).
Note: Logged out of AWS
Note: Logged into Local Computer
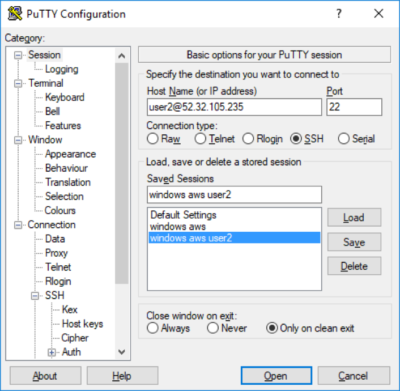
Now, the keys need to be downloaded to the local machine to access the AWS instance via SSH as user2. The process is different depending on whether your local computer is a Mac or Windows PC.
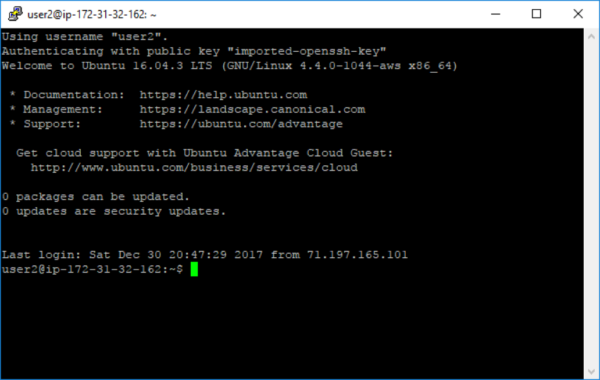
Note: Logged into AWS
If the connection to AWS as user2 is successful, then remove files from /tmp2 and the folder itself:
cd /tmp2 sudo rm authorized_keys sudo rm id_user2 sudo rm id_user2.pub cd .. sudo rm –d /tmp2
Removing Ubuntu login access:
It is a good practice from a security perspective, to remove SSH access for Ubuntu default user (root) logins.
Log in as user2 to edit the sshd_config file:
sudo nano /etc/ssh/sshd_config
Remove ubuntu from the line:
AllowUsers user2
Modify, if needed, the following line:
PermitRootLogin no
Then, ctrl-x, type y, and return to save.
Restart the ssh service:
sudo systemctl restart ssh.service
Updates to Ubuntu:
With a new instance, it is time to apply any updates to Ubuntu 20.04 that may be needed. Follow the steps in A Collection of AWS EC2 Ubuntu Tips, Section: Updates to Ubuntu.
That’s it. Linux Ubuntu instance is established and running, alternate user is established, keys have been created, and Ubuntu updates have been applied.